WHAT CAN XSETTE DO FOR YOU?
WHO USES XSETTE TECHNOLOGY
XSETTE Technology is a software solution for securing ALL digital content and critical infastructure. It is capable of protecting any digital file including music, movies, digital books, Office Documents, pictures, medical records, banking records, email, text and any other type of digital content. It can also protect streaming audio and video from being redirected.
SAMPLE PROBLEM #1
HOW WOULD XSETTE SOLVE THIS?
Our node pairing technology ensures that login data is only applicable on the device in which it was intended. Any other device using this data would be shut out. The owner can immediately lock the account down for security. Even if a thief obtains your login credentials, they are useless on an unathorized machine.
SAMPLE PROBLEM #2
MOVIE SCREENERS ARE NOT SAFE.
Academy screeners/Movie Dalies/recordings are distributed via screeners. While currently protected with a 4-key password, they are easily hacked, stolen and distributed, costing studios millions of dollars.

HOW WOULD XSETTE SOLVE THIS?
Our Node Pairing and BMUS technology allows content to be restriced to the device in which it was intended, including DVD players, computers and mobile devices. Only preregistered devices would be allowed access any media content.
SAMPLE PROBLEM #3
HOW WOULD XSETTE SOLVE THIS?

XSETTE Technology can lock down all files and data within a network. All files, regardless of the type cannot be accessed by anyone not on an assigned machine. This includes emails, office files or information stored on an internal server.
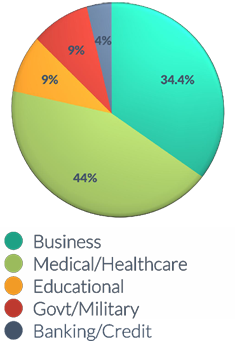
WHERE ARE THE BREACHES OCCURING
WE ALSO OFFER MOBILE PROTECTION
Proactive Security: Reduce the Risk of a Breach
Stay ahead of cyber threats with XSETTE’s advanced security approach. Our comprehensive strategies go beyond traditional methods to ensure your data remains safe, secure, and resilient against breaches.
01
Going beyond automated testing
Uncover hidden vulnerabilities with advanced security assessments.
02
Developing a threat model
Identify and mitigate risks with a tailored threat model.
03
Protect proactively
Prevent breaches with real-time monitoring and security measures.
04
Detailed application security report
Comprehensive insights for stronger data protection
Testing Comparison Chart
Lorem ipsum dolor sit amet consectetur adipiscing elit odio aliquam.
DevSecOps
Application Testing
DevSecOps
Application Testing
general question
Frequently Asked Questions
We provide a myriad of services and know getting the right support is overwhelming. Sourcing our frequently asked questions, we want to help and provide you with the service that is right for you.
XSETTE offers a comprehensive, next-generation approach to security, combining personal protection, cloud security, and digital file encryption with cutting-edge technology and over 20 years of expertise.
We use advanced encryption, real-time threat monitoring, and proactive mitigation strategies to protect your data from cyber threats, unauthorized access, and breaches.
Yes! Whether you're an individual looking to safeguard personal information or a business securing critical data, XSETTE provides tailored solutions to meet your needs.
Absolutely. XSETTE is designed to secure data across all platforms, including cloud networks, mobile devices, and streaming services.
Simply schedule a consultation with our experts. We'll assess your security needs, create a custom plan, and implement a holistic program to keep your data safe.








